Thanks for requesting your Cybersecurity Awareness Month Resource Kit
We hope these help you and your users defend against cybercrime!
Cybersecurity Awareness Month is a great time to educate yourself and your users.
Threats to your organization can come in many forms; from a suspicious email with a dodgy attachment to improperly stored sensitive information.
But never fear! The team featured in KnowBe4’s award-winning, streaming-quality educational series “The Inside Man,” is here to lend a helping hand. Our 2024 Cybersecurity Awareness Month resource kit delivers an immersive, multimedia cybersecurity awareness training experience centered around the gripping "The Inside Man" original series.
For you: our most popular security awareness on-demand webinar and whitepaper, resources for planning your training, and new templates to use in your campaigns. For your users: suggested training, infographics, new Inside Man character posters, plus new newsletters, security docs, and awareness tips that will help to keep them on their toes with security top of mind.
Resources for Planning Your Training
Cybersecurity Awareness Month Guide
This guide walks you through user resources included in your kit, suggestions for how to use them, and campaign ideas to get you started.
View GuideCybersecurity Awareness Weekly Planner
This web-based training planner is packed with all of the great resources for users you see below. We put them into a weekly plan as an example for when to send each of the resources to your users.
View PlannerResources for You
Support Documentation
- BONUS: Gamification Options for Cybersecurity Awareness Month 2024 PDF
- BONUS: The Inside Man Watch Party Facilitators Guide
- NOTE: All resources below can be found by searching for the title in your admin console
New Phishing Templates
Google Drive: Security Update
OpenAI: You have been invited to a ChatGPT Team
IT: Mobile Phone Security (Spoofs Domain)
Microsoft 365: Help us protect you - Security advice for your email account
New Landing Page Templates

Inside Man New Recruits: “Basic Oops!”

Inside Man: “Basic Oops!”
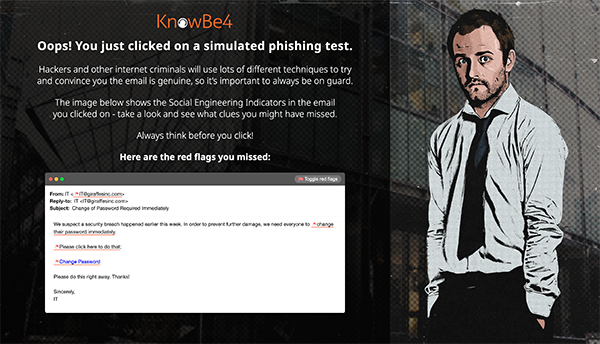
Inside Man New Recruits: SEI Rules to Stay Safe Online
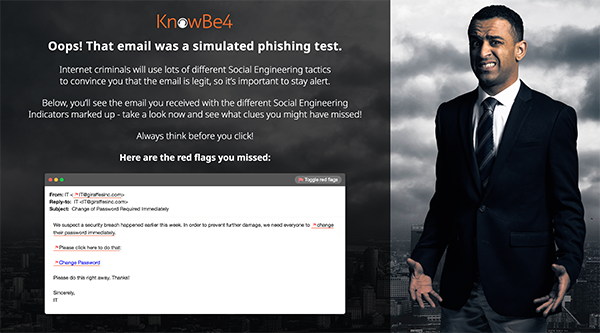
Inside Man: SEI Rules to Stay Safe Online
Resources for Your Users
Interactive Training Modules

New Interactive Mini-Game - The Inside Man: New Recruits
"The Inside Man: New Recruits" makes your users part of the series as they help protect the Khromacom corporation from possible hackers. They’ll be recruited by series lead Mark Shepherd and interact with many other characters as they complete challenges related to password security, document handling, physical security, social media sharing, phishing and more.
Get a KMSAT demo
Request a live product demo
Video Modules

Reality Bytes - Business Email Compromise (BEC)

Confessions of a ChatGPT Novice

Security Snapshots: “Travel Travails” (Travel Security)

Incident Response: First Steps
New The Inside Man Character Cards and Posters
Mark Shepherd
AJ
Fiona
Maurice (The Handler)
New Security Hints & Tips Messages
These messages can help keep your users informed about security threats and help reinforce the topics they learn about in their security training.
Click each message name to download a zip file with translations in 12 languages!
Security Docs and Awareness Tips
These will show your users what to watch out for in emails as well as how to use AI safely, and how to work securely from home or the office.

The Human Firewall Manifesto

Don't Let Them Phish Your Inbox
.png)
QR Codes: Enjoy Safe Scanning

How to Spot a Deepfake

AI and Cybercrime

Using Artificial Intelligence Safely and Securely

Data Privacy at Work and at Home
Mobile Device Security Tips
.png)
Taking Home Security Awareness

Following Policy and Reporting Incidents

First Steps Series: Working on Security Culture

Cyber Heroes Series: Tailgating/Stranger Danger
Follow KnowBe4 for More Resources
For more resources, tips, and news for you and your users throughout cybersecurity awareness month be sure to follow and mention @KnowBe4 on social media. Use the hashtag #SecureOurWorld to stay in the loop throughout Cybersecurity Awareness Month!











